... does not interpret the bits in the access mask; instead, it compares them to the object’s protection mask (CHP$_PROT). Any bits not specified by ...
15 KB (2,536 words) - 09:56, 8 June 2019
... does not have the privilege to read or write to this mailbox. (The protection mask is defined when the mailbox is created.) The flags parameter to ...
122 KB (18,338 words) - 07:03, 23 December 2019
... the process UIC. If the prot argument is nonzero, it replaces the protection mask from the template. On Alpha or Integrity server systems , the flag ...
27 KB (4,468 words) - 12:46, 28 November 2019
... non-paged pool. promsk SyservArgument file_protection longword (unsigned) read only by value Protection mask to be associated with the ...
15 KB (2,430 words) - 12:45, 28 November 2019
... fields: the user field and a group field. System objects also have a protection mask that allows read, write, execute, and delete access to the object ...
73 KB (10,966 words) - 01:24, 5 June 2022
 | File:ZK-1706-GE.png Diagram depicting the protection mask for $CRMPSC
(257 × 70 (8 KB)) - 06:40, 10 July 2019 |
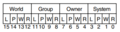 | File:Снимок.png ZK-1707-GE Diagram of $CREMBX promsk protection mask
(352 × 94 (12 KB)) - 18:49, 23 July 2019 |
... can be used to buffer messages sent to the mailbox : promsk:int : protection mask to be associated with the created mailbox : acmode:int : access mode ...
37 KB (5,969 words) - 23:26, 6 July 2022
... _EFWM Returns the event flag wait mask of the process, which is a longword ... Returns the default UIC Protection file protection . - JPI$_RMS ...
49 KB (8,143 words) - 07:47, 14 November 2019
... flags mask_longword read only by value Mask specifying ... mode to be used in the object protection check. The acmode argument is the address ...
13 KB (2,135 words) - 10:47, 3 February 2020
... defines these names. You form the bit mask by specifying the symbolic name of each ... _VOLPRO Override volume protection - WORLD PRV$M_WORLD ...
13 KB (2,104 words) - 07:14, 9 July 2019
... style="text-align:center;" String The volume Protection mask protection mask - WRITETHRU_CACHE_ENABLED style="text-align:center ...
37 KB (5,607 words) - 11:27, 28 October 2022
... the result by 8. - SYI$_AVAIL_CPU_MASK Note that this item code is becoming ... to create and maintain protected subsystems by assigning the ...
54 KB (8,797 words) - 19:32, 13 November 2019
... Reference Manual for more information about specifying protection masks.) By default, the mask is 64000 (decimal) or FA00 (hexadecimal), which ...
982 bytes (145 words) - 16:32, 30 June 2019
... You can also obtain the values as masks with the appropriate bit set using the ... to create and maintain protected subsystems by assigning the ...
4 KB (550 words) - 07:17, 9 July 2019
... You can also obtain the values as masks with the appropriate bit set using the ... to create and maintain protected subsystems by assigning the ...
5 KB (698 words) - 12:23, 15 July 2019
... - 4 Allows security profile changes to protected objects on a local node when the ... SIGNON logical name bit mask value 4 for LOGINOUT. - 10 ...
3 KB (446 words) - 16:05, 1 July 2019
... _COUNT QUI$_PROCESSOR QUI$_PROTECTION QUI$_QUEUE_DESCRIPTION QUI$ ... Each bit set in the bit mask represents a characteristic number in the range ...
47 KB (7,858 words) - 12:47, 28 November 2019
... _FLAGS A longword containing a mask of flags that indicates ... This is typically used to visually protect sensitive data, such as password information. ...
29 KB (4,677 words) - 11:15, 23 March 2022

